Table of contents
- Pre-requisites
- Introduction
- Step-01: Copy all files from previous section
- Step-02: c5-05-securitygroup-loadbalancersg.tf
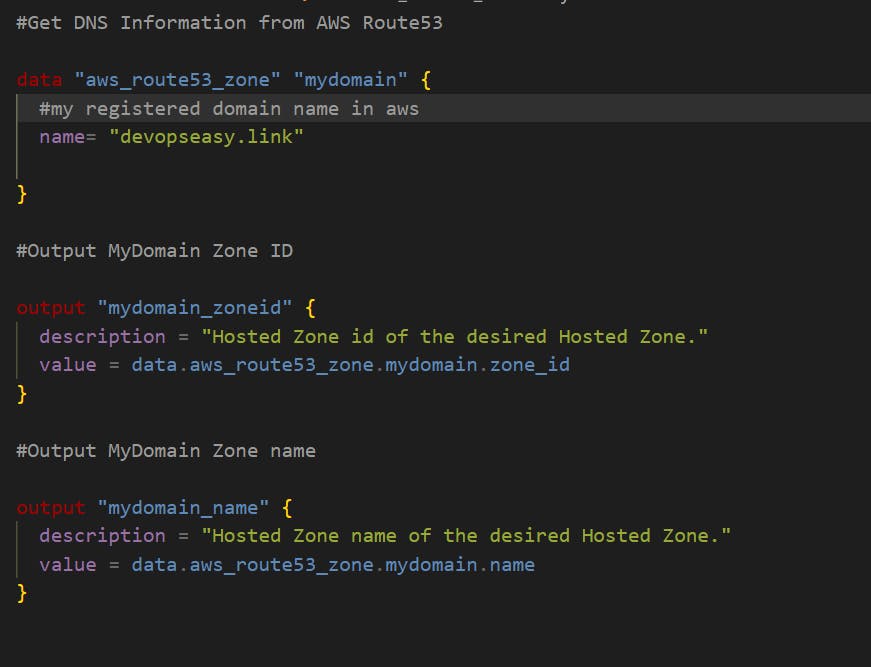
- Step-03: c6-02-datasource-route53-zone.tf
- Step-05: c11-acm-certificatemanager.tf
- Step-05: c11-acm-certificatemanager.tf
- Step-06: c10-02-ALB-application-loadbalancer.tf
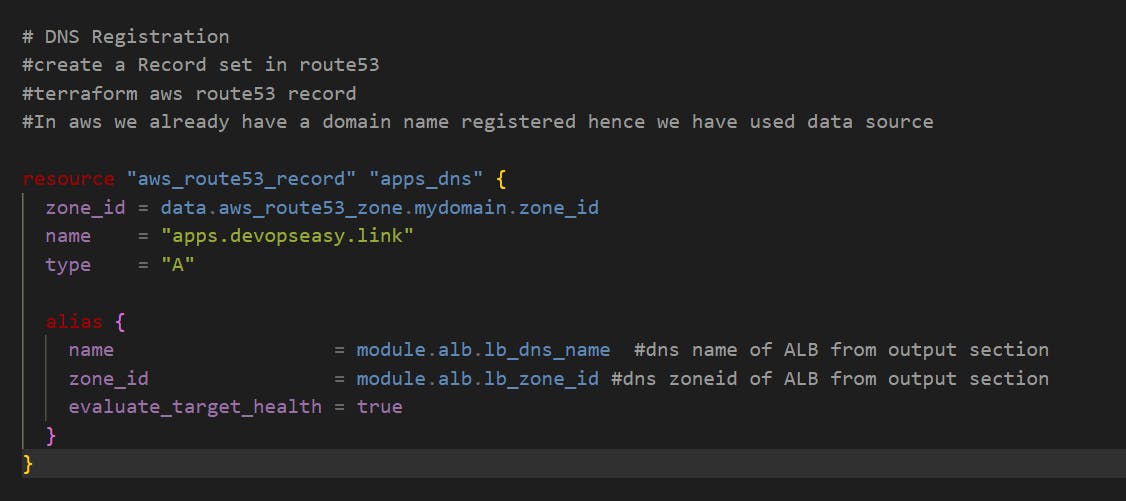
- Step-07: c12-route53-dnsregistration.tf
- Step-08: Execute Terraform Commands
- Step-09: Clean-Up
- Results:
Hello Everyone,
Today we will be deploying a 3-tier Context Path Based ALB using Terraform in AWS.
Previously I used a simple Application load balancer so this is an upgrade to project2.
Services used are EC2 Instances, VPC, Nat gateway, Internet Gateway, security groups, ACM, Route53, and Application Load balancer
GitHub link:- https://github.com/piya199616/Terrraform-AWS-Project3.git
Project2 link:- https://priyanka-burela.hashnode.dev/deploy-3-tier-ha-application-load-balancer-using-terraform-in-aws
Link for Manual Creation of Route53 with ACM certificate:
https://priyanka-burela.hashnode.dev/aws-certificate-manager-dns-validation
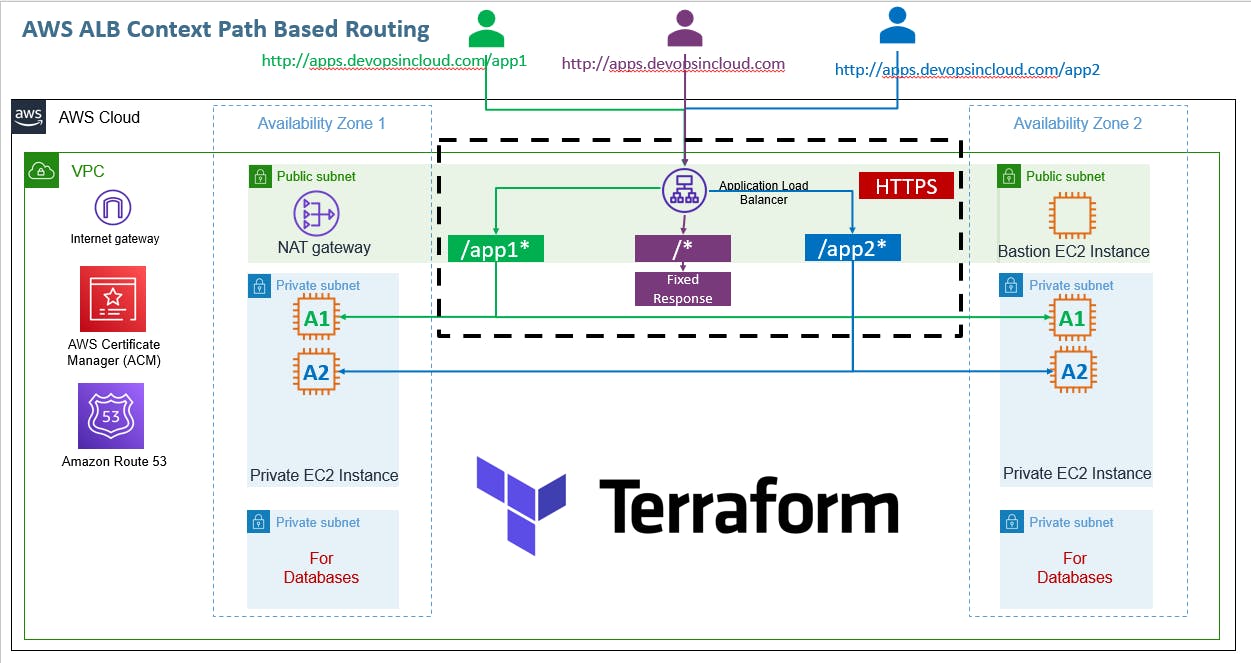
Project Diagram:-
Pre-requisites
AWS Account
Terraform installed in the local system
AWS CLI installed in the Local system
Knowledge of AWS and Terraform.
You need a Registered Domain in AWS Route53 to implement this use case.
Introduction
We are going to implement Context Path-based Routing in AWS Application Load Balancer using Terraform.
To achieve that we are going to implement many series of steps.
Our core focus in the entire section should be primarily targeted to two things
Listener Indexes:
https_listener_index = 0Target Group Indexes:
target_group_index = 0
If we are good at understanding these indexes and how to reference them, we are good with handling these multiple context paths or multiple header-based routes or anything from ALB perspective.
We are going to implement the following using AWS ALB
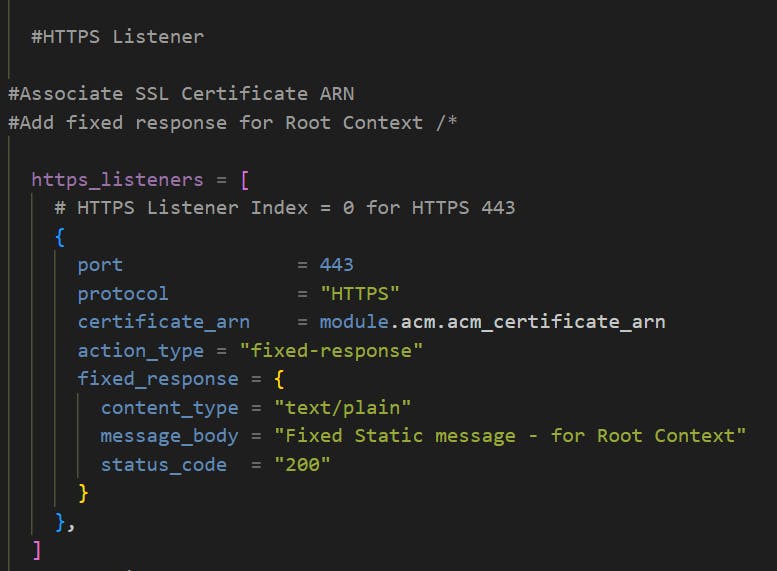
Fixed Response for /* : http://apps.devopseasy.link
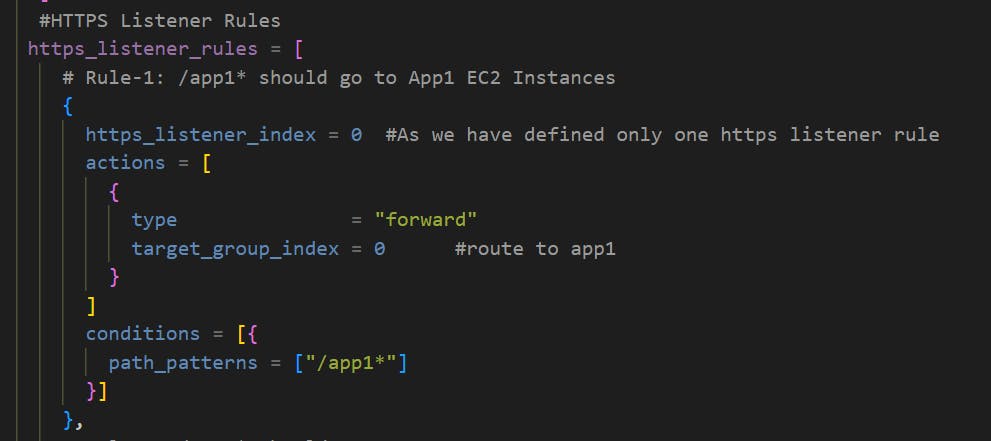
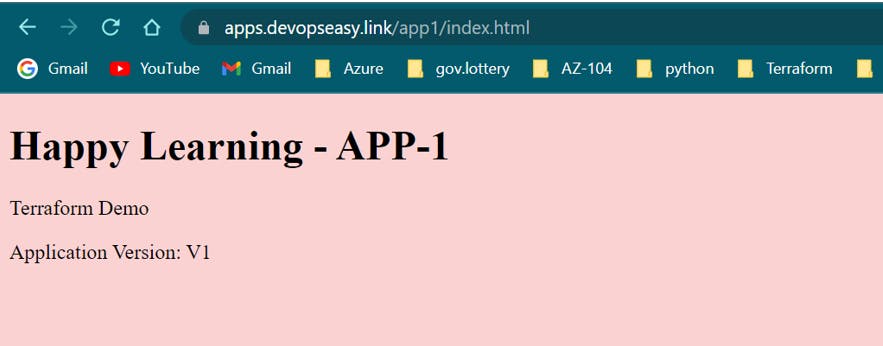
App1 /app1* goes to App1 EC2 Instances: http://apps.devopseasy.link/app1/index.html
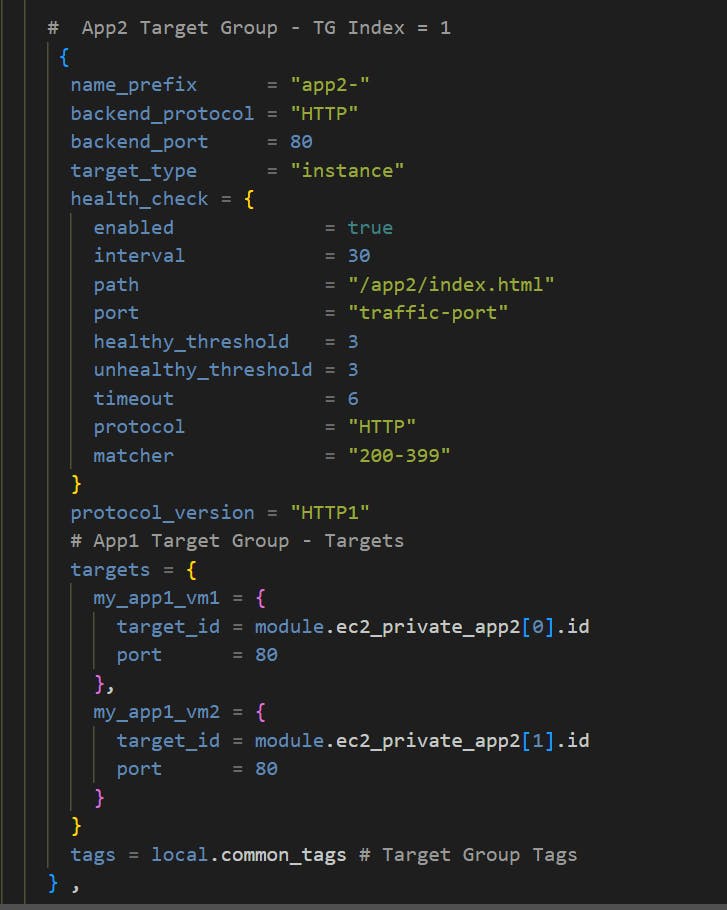
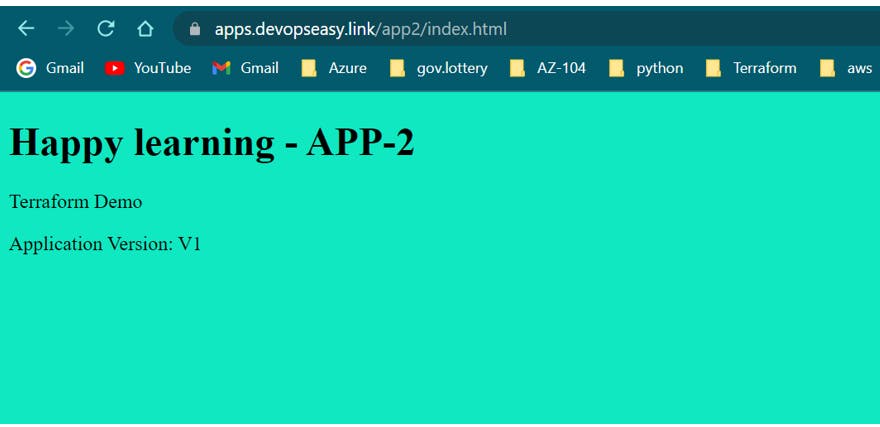
App2 /app2* goes to App2 EC2 Instances: http://apps.devopseasy.link/app2/index.html
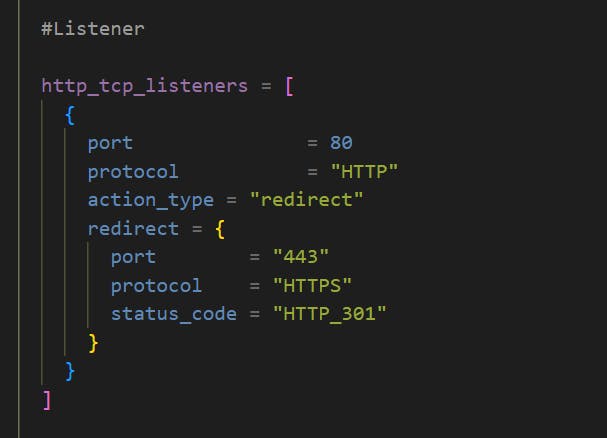
HTTP to HTTPS Redirect
Step-01: Copy all files from previous section
We are going to copy all files from
c1 to c10 from Project2.Create new files
Review the files
Step-02: c5-05-securitygroup-loadbalancersg.tf
Update load balancer security group to allow port 443
ingress_rules = ["http-80-tcp", "https-443-tcp"]
Step-03: c6-02-datasource-route53-zone.tf
- Define the datasource for Route53 Zone
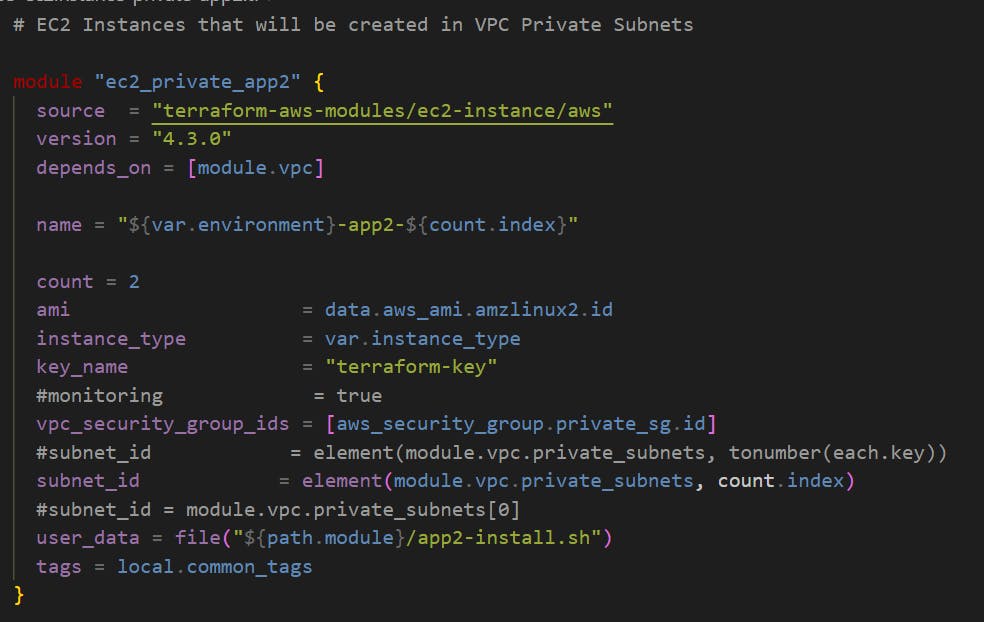
Step-04: c7-05-ec2instance-private-app2.tf
Create new EC2 Instances for App2 Application
Module Name: ec2_private_app2
Name: "${var.environment}-app2"
User Data: user_data = file("${path.module}/app2-install.sh")
Step-05: c11-acm-certificatemanager.tf
Create a SAN SSL Certificate using DNS Validation with Route53
This is required for us with ALB Load Balancer HTTPS Listener to associate SSL certificate to it
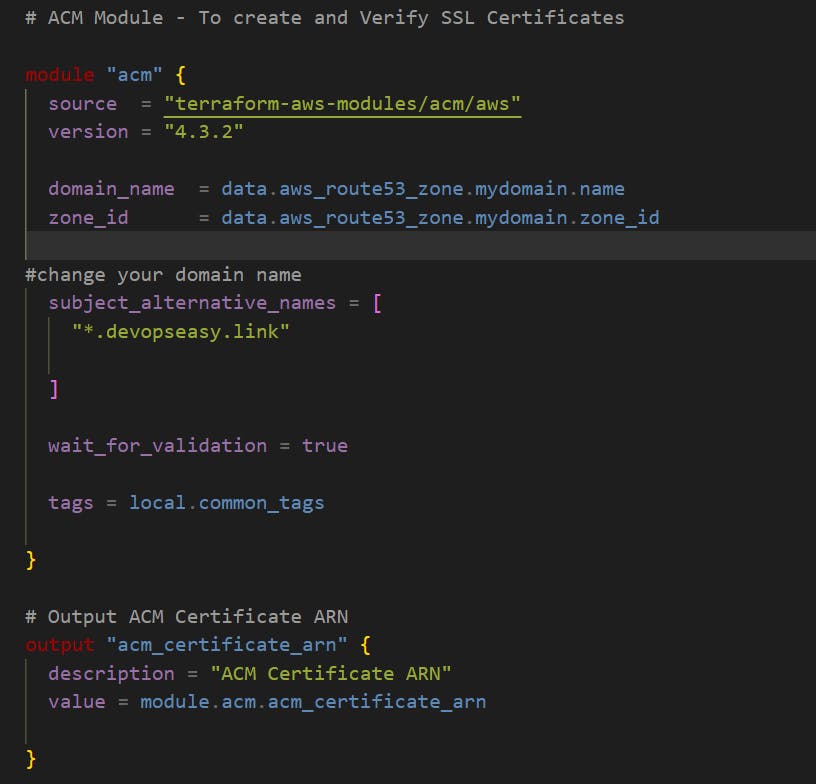
Step-05: c11-acm-certificatemanager.tf
Create a SAN SSL Certificate using DNS Validation with Route53
This is required for us with ALB Load Balancer HTTPS Listener to associate SSL certificate to it
Step-06: c10-02-ALB-application-loadbalancer.tf
Step-06-01: HTTP to HTTPS Redirect
Step-06-02: Add Target Group app2
Step-06-03: Add HTTPS Listener
Associate SSL Certificate ARN
Add fixed response for Root Context
/*
Step-06-04: Add HTTPS Listener Rules
Understand about https_listener_index
Create Rule-1: /app1* should go to App1 EC2 Instances
Understand about target_group_index
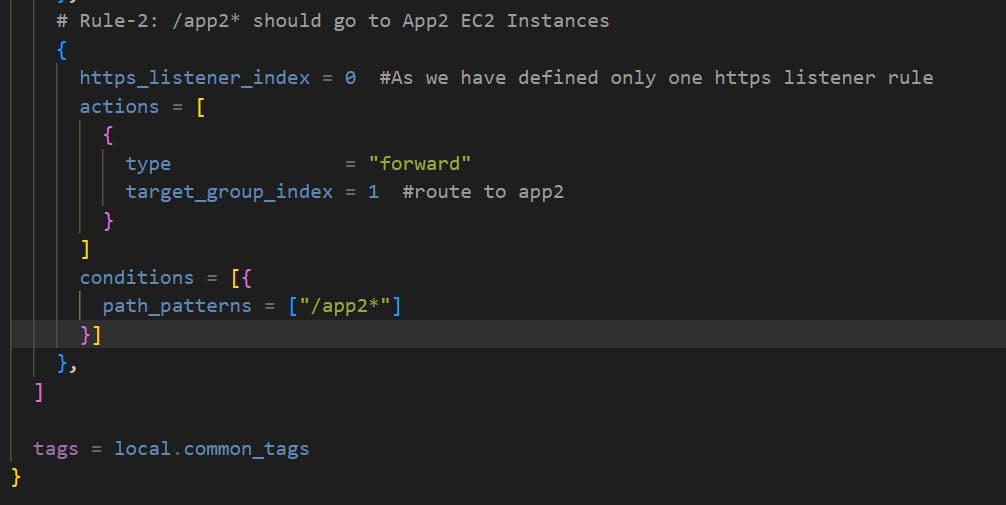
Create Rule-2: /app2* should go to App2 EC2 Instances
Step-07: c12-route53-dnsregistration.tf
Step-08: Execute Terraform Commands
# Terraform Initialize
terraform init
# Terraform Validate
terraform validate
# Terraform Plan
terraform plan
# Terraform Apply
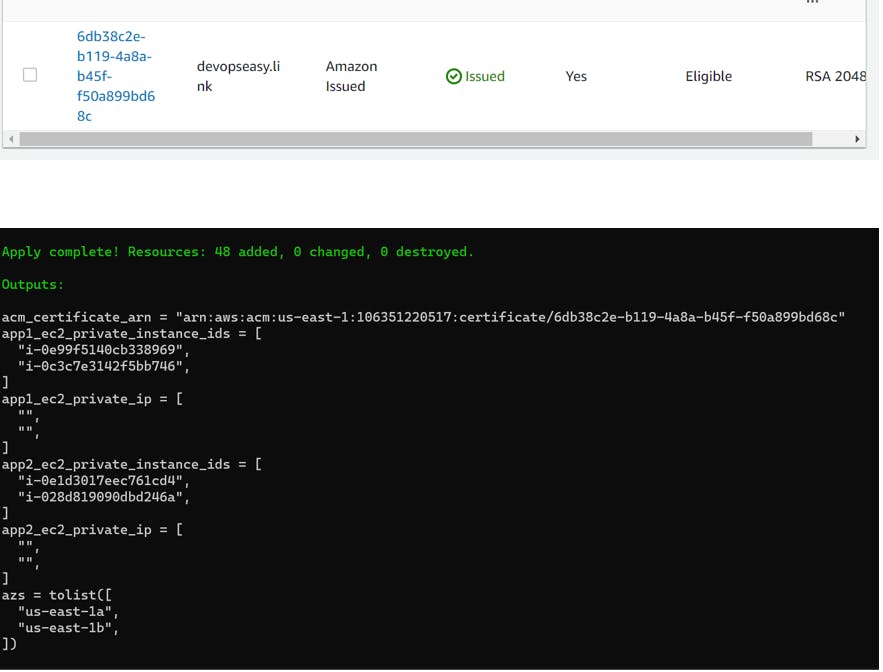
terraform apply -auto-approve
# Verify
Observation:
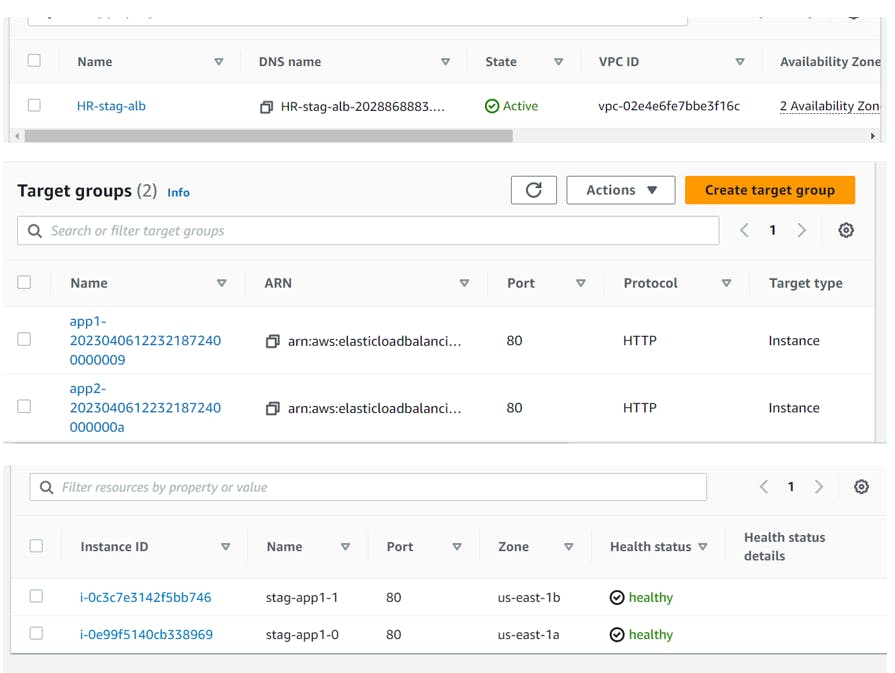
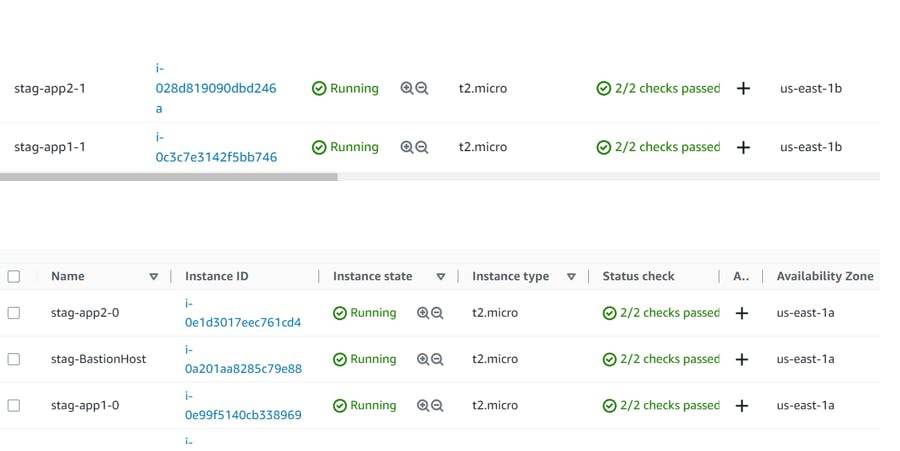
1. Verify EC2 Instances for App1
2. Verify EC2 Instances for App2
3. Verify Load Balancer SG - Primarily SSL 443 Rule
4. Verify ALB Listener - HTTP:80 - Should contain a redirect from HTTP to HTTPS
5. Verify ALB Listener - HTTPS:443 - Should contain 3 rules
5.1 /app1* to app1-tg
5.2 /app2* to app2-tg
5.3 /* return Fixed response
6. Verify ALB Target Groups App1 and App2, Targets (should be healthy)
5. Verify SSL Certificate (Certificate Manager)
6. Verify Route53 DNS Record
# Test (Domain will be different for you based on your registered domain)
# Note: All the below URLS should redirect from HTTP to HTTPS
1. Fixed Response: http://apps.devopseasy.link
2. App1 Landing Page: http://apps.devopseasy.link/app1/index.html
3. App1 Metadata Page: http://apps.devopseasy.link/app1/metadata.html
4. App2 Landing Page: http://apps.devopseasy.link/app2/index.html
5. App2 Metadata Page: http://apps.devopseasy.link/app2/metadata.html
Step-09: Clean-Up
# Terraform Destroy
terraform destroy -auto-approve
Results:
#KeepLearningKeepSharing
Thank you for reading my blog, Hope you found this helpful.
If you need any help then feel free to ping me on Linkedin: